A Secure Access Approach to English Language Education Networks for Edge Computing
, und
17. März 2025
Über diesen Artikel
Online veröffentlicht: 17. März 2025
Eingereicht: 27. Okt. 2024
Akzeptiert: 08. Feb. 2025
DOI: https://doi.org/10.2478/amns-2025-0193
Schlüsselwörter
© 2025 Lili Jin et al., published by Sciendo
This work is licensed under the Creative Commons Attribution 4.0 International License.
Figure 1.
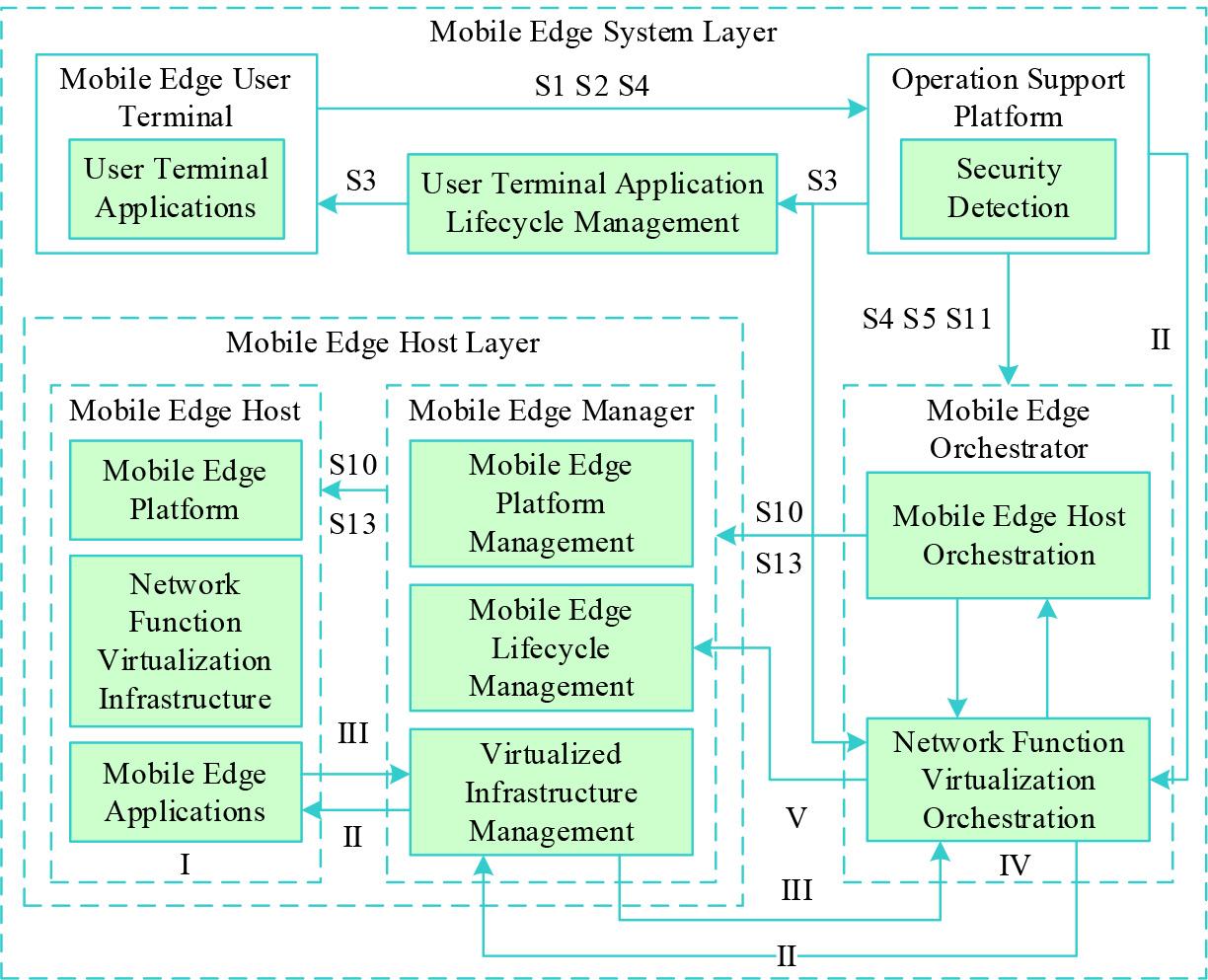
Figure 2.
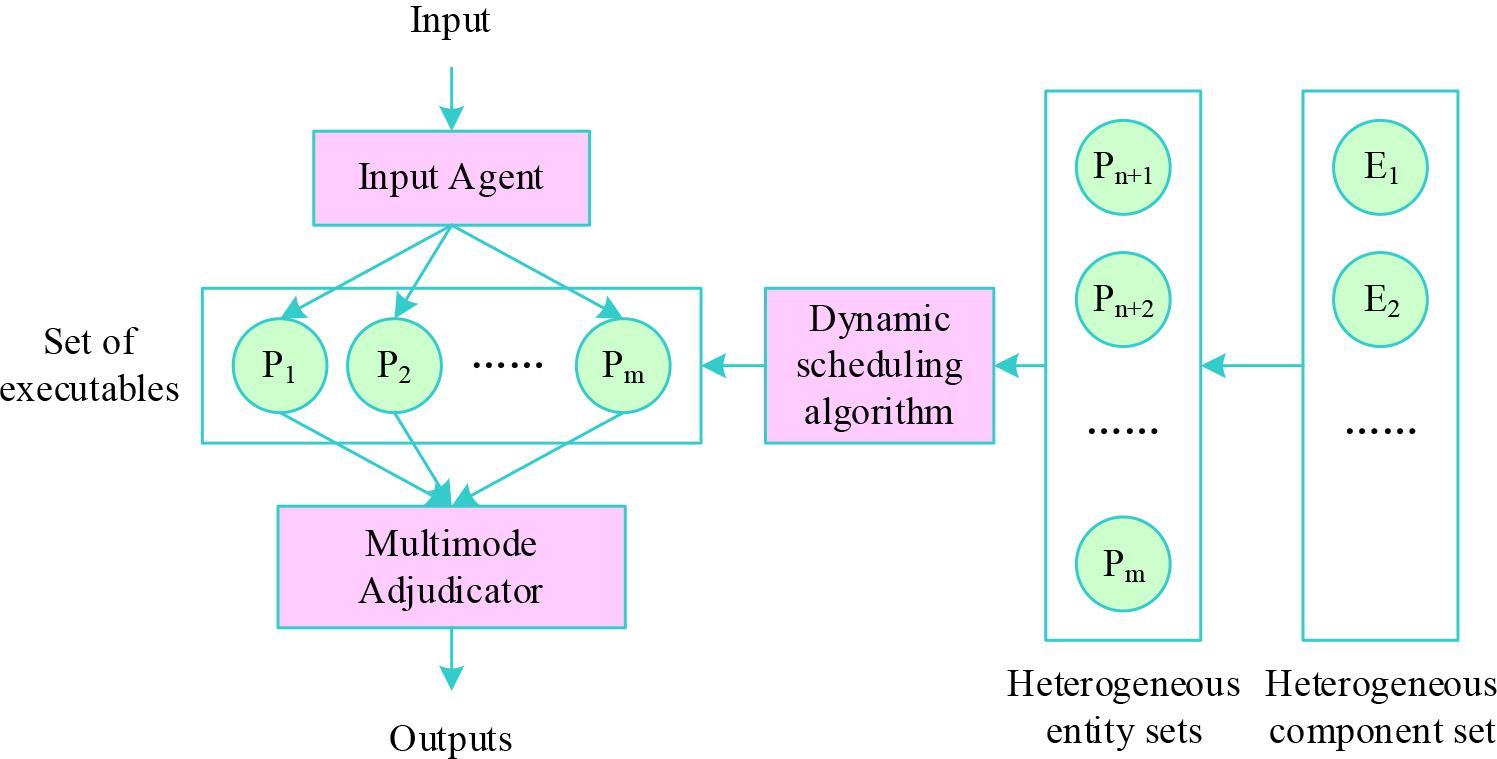
Figure 3.
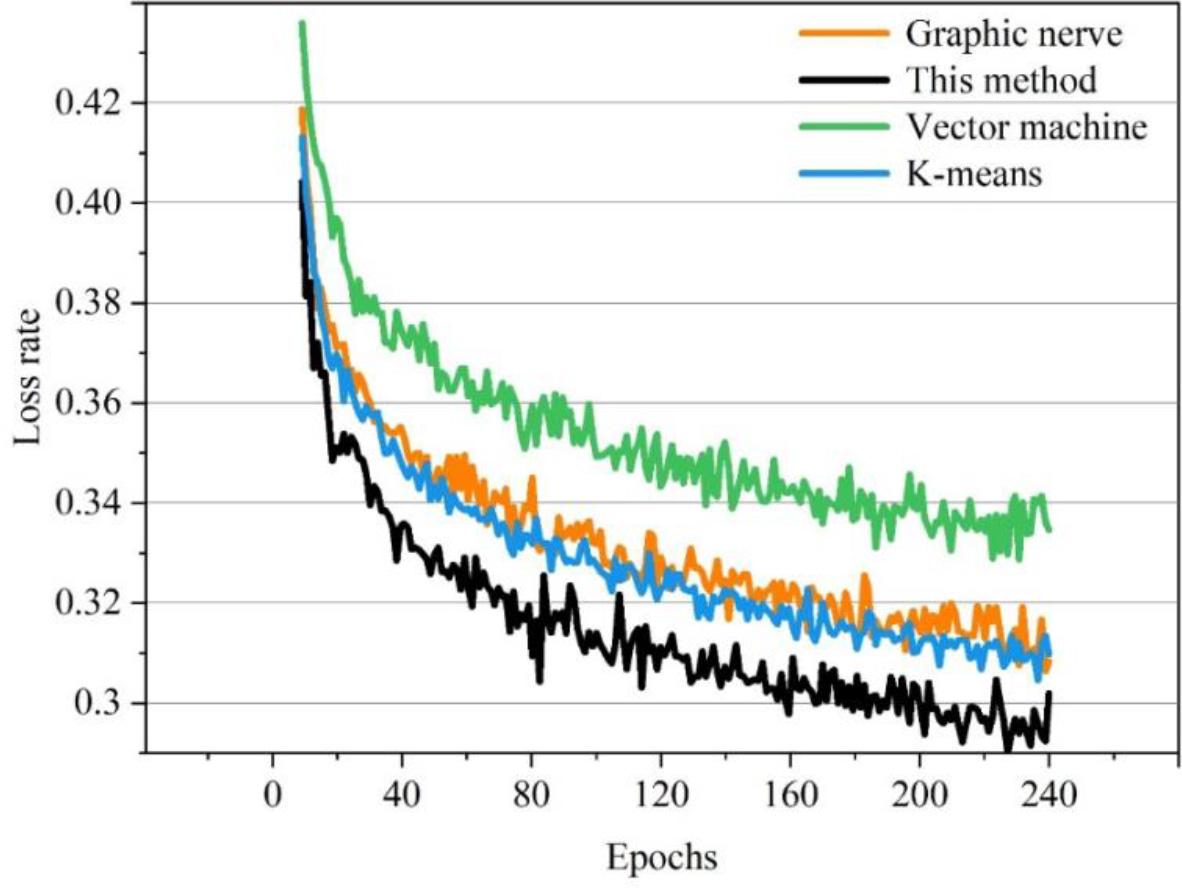
Figure 4.

Figure 5.
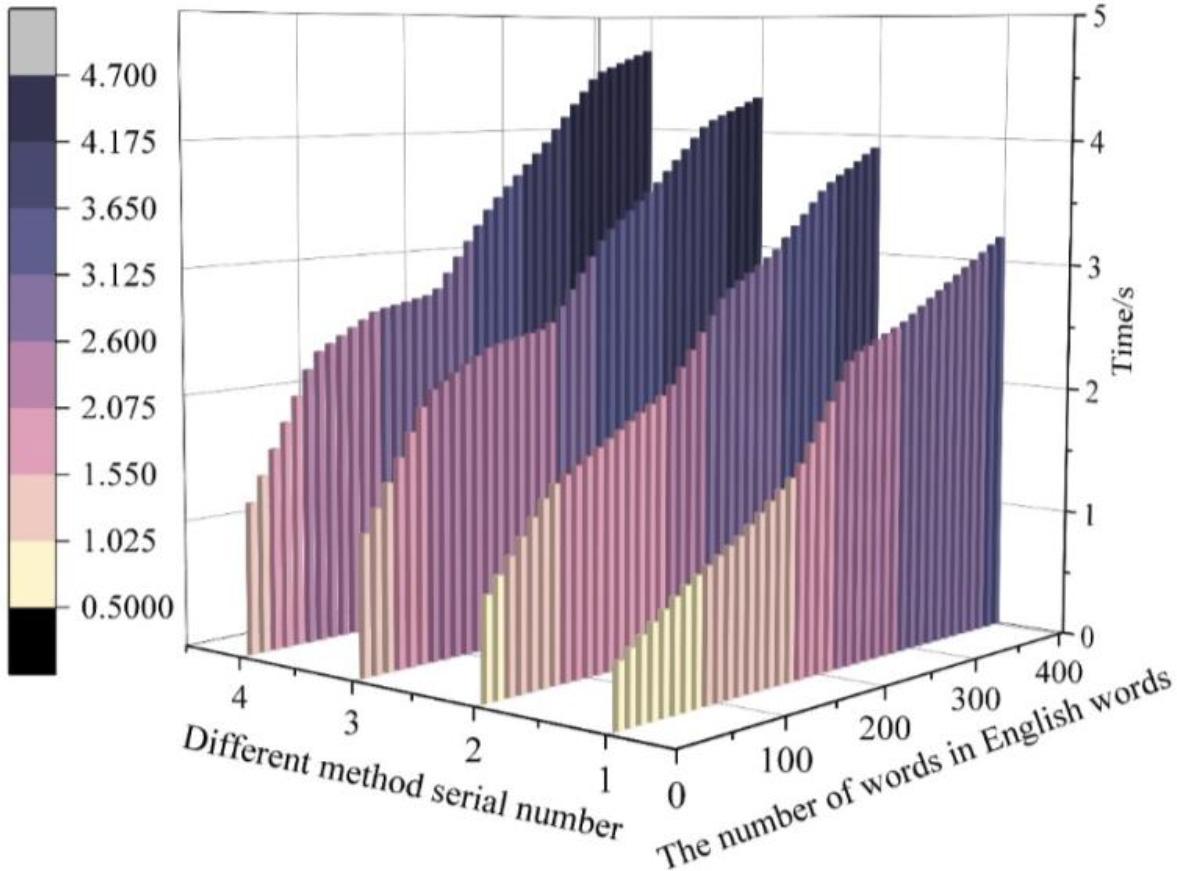
Figure 6.
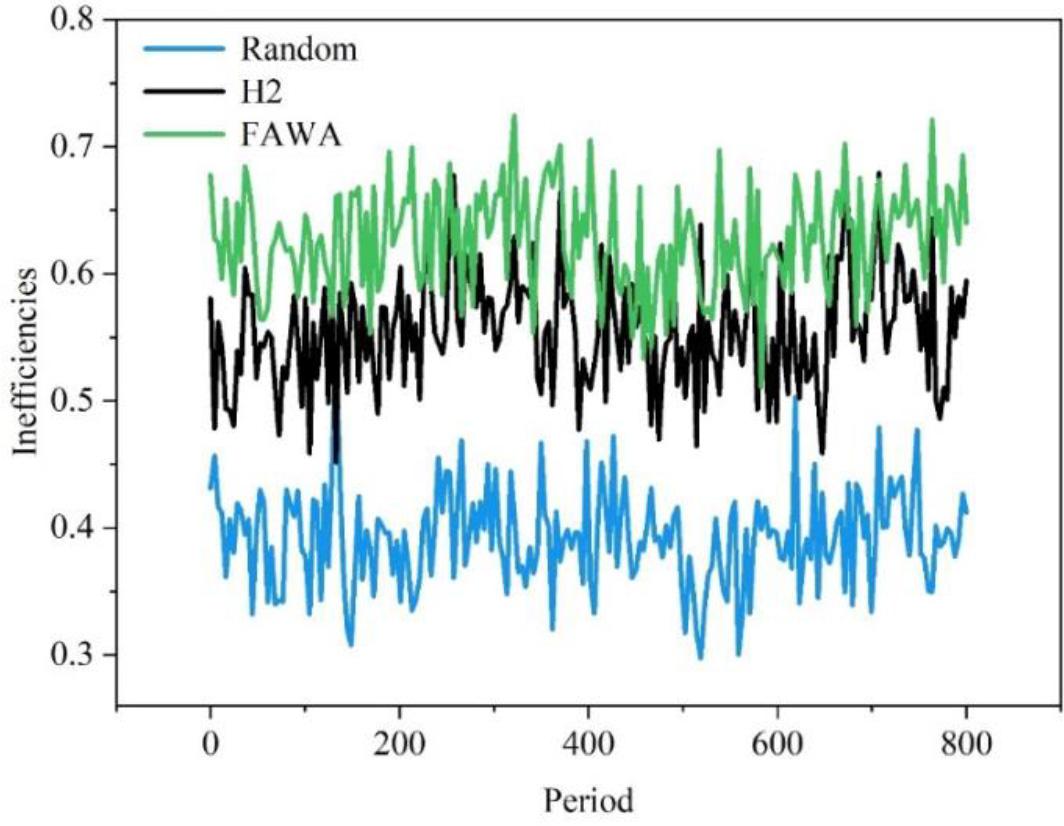
Data distribution
| Data set | Type | Training set | Test set |
|---|---|---|---|
| UNSW-NB15 | Analysis | 1754 | 1105 |
| Backdoors | 1258 | 1057 | |
| Do S | 8359 | 7546 | |
| Exploits | 25486 | 18934 | |
| Fuzzers | 14562 | 12548 | |
| Generic | 113598 | 105365 | |
| Normal | 1608413 | 1245339 | |
| Reconnaissance | 7618 | 4586 | |
| Shellcode | 847 | 754 | |
| Worms | 126 | 95 | |
| CICIDS2017 | Benign | 1054921 | 1014532 |
| Botnet | 1548 | 1254 | |
| Brute Force | 11693 | 10258 | |
| DDoS | 105486 | 84521 | |
| DoS | 122846 | 102546 | |
| Port Scan | 102935 | 95125 | |
| Web Attack | 1058 | 1254 |
This article is part of the safety plan
| No.1 | No.2 | No.3 | No.4 | No.5 | No.6 | No.7 | |
|---|---|---|---|---|---|---|---|
| Comprehensive score | 8.5 | 3.38 | 7.4 | 8.4 | 3.5 | 3.97 | 2.8 |
| Attack no. 2 after the total score | 8.5 | 7.56 | 7.4 | 8.46 | 3.4 | 3.8 | 2.7 |
| Attack no. 13 after the total score | 8.2 | 3.35 | 2.56 | 8.44 | 3.56 | 3.78 | 2.69 |
| Attack no. 14 after the total score | 8.12 | 3.46 | 7.14 | 8.41 | 9.46 | 3.45 | 2.94 |
| Attack no. 17 after the total score | 8.16 | 3.41 | 7.45 | 8.28 | 3.59 | 9.46 | 10.24 |
Random generated execution body
| Execution number | Loophole | The current situation of the five periodic tables |
|---|---|---|
| 1 | 1, 4, 5, 6, 7 | [0 1 0 0 0] |
| 2 | 2, 4, 6, 15 | [0 0 0 1 1] |
| 3 | 4, 7, 9, 11, 13 | [0 1 1 0 0] |
| 4 | 8, 5, 6, 12, 16 | [0 0 0 0 1] |
| 5 | 14, 15, 16 | [0 0 0 1 0] |
| 6 | 17, 18, 19 | [0 0 1 0 0] |
| 7 | 17, 10, 11 | [0 0 0 1 0] |
